These Are the Conditions Outlined by Prisma Finance’s Hacker

[ad_1]
The hacker behind the $11.6 million breach on Prisma Finance has outlined conditions for returning the stolen funds.
In an on-chain message, the self-proclaimed white hat hacker lamented the team’s slow response.
Hacker Details Conditions to Return Prisma Finance Funds
On March 28, DeFi protocol Prisma Finance reported a security breach that led to the loss of 3,257.57 wstETH, worth $11.6 million. Since then, the project has urged its users to revoke delegate approvals and released a comprehensive post-mortem audit about the incident.
According to Prisma Finance, the hacker exploited a vulnerability in both versions of the project’s MigrateTroveZap (mkUSD and ULTRA) contracts, and around 20 addresses remain affected.
The Prisma Finance hacker now demands that the project conduct an online press conference where all team members would reveal their identities. He also wants the team to address past mistakes, disclose the smart contract’s auditor, and present plans for enhancing security measures.
Besides that, Prisma Finance must also inform the community about contract deployment strategies and emergency response protocols.
Read more: Identifying & Exploring Risk on DeFi Lending Protocols
The hacker also expressed dissatisfaction with terms like “exploit” and “attack” in the post-mortem audit. He emphasized that the illicit transactions were in line with smart contract terms agreed upon by all parties.
“You cannot agree something with others, and then judge it is wrong or it is true. No human rights. You should have been more careful before deploying your contract. I hope this would help people be more careful participating in defi, the teams would be more responsible, and everyone would change their minds about things like this,” the hacker wrote.
Consequently, the hacker refuted claims of malicious intent. He further urged Prisma Finance to retract the accusatory language within 12 hours.
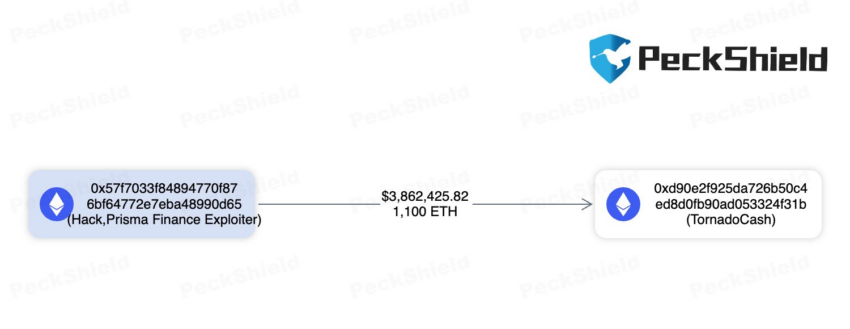
Despite these demands to return the stolen funds, the crypto community questions the attacker’s status as a white hat hacker.
He has utilized the OFAC-sanctioned crypto mixing tool Tornado Cash to obfuscate his transactions. Blockchain security firm Peckshield reported that addresses belonging to the hacker moved more than 1,000 ETH through the mixer. Regardless, the hacker continues to ensure that stolen funds will be returned.
“After [the online conference] happens, the amount I would keep, and the amount that I can send to you would be discussed (stay assured, most of it would be returned) and the notes would be sent to your email,” the hacker added.
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.
[ad_2]
Source link
